Web 3 Penetration Testing
Take a proactive approach to security. Find your project’s flaws before attackers do. CertiK’s Web3 penetration testing service explores and exploits wallets, exchanges, Dapps, using the same expertise and tools as black hat hackers in order to protect against them.
Web3 Security For Wallets, Exchanges & Dapps
A comprehensive approach to testing your Wallets, Exchanges and Dapps in a Web3 environment.

Web3 Network & Application Testing
We perform dynamic testing at both the network and application-level in order to uncover the most complex vulnerabilities

Web & Mobile Apps Coverage
Continuous security assessment of both web and mobile applications

Web3 Security Expertise
Our penetration testers have deep knowledge of web3 applications and experience auditing thousands of lines of code
What is Web3 Penetration Testing?
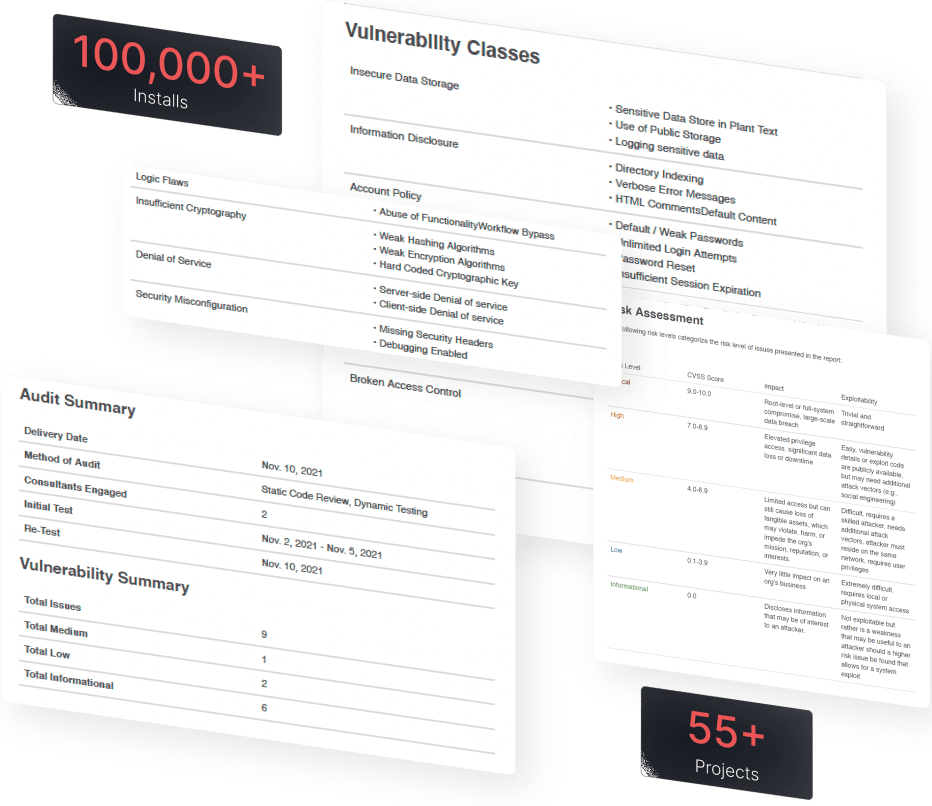
Web3 Penetration testing involves taking an offensive approach to security auditing. Penetration testers utilize the same tools as black hat hackers in order to detect and remediate vulnerabilities before bad actors can exploit them.
While Web2 penetration testing has been around for quite some time, when it comes to Web3 there are new variables to consider. Web3 Penetration testers must have a comprehensive understanding of blockchain technology, smart contracts, NFT functionality, and more in order to perform a comprehensive penetration test. As many decentralized applications also utilize Web 2.0 and earlier technology, penetration testers must be well versed in all aspects of network security.

Our Approach to Penetration Testing
Our Web3 Penetration Testing services uncover even the smallest weaknesses by leveraging both standard and proprietary tooling, as well as previously found vulnerabilities, powered by an experienced team of ethical hackers.
Our Web 3 Penetration Testing Process
Our Web3 penetration testing process includes seven key steps.